- Published on
Core Rule Set: Install Microsoft IIS with ModSecurity and the Core Rule Set on Windows Server 2022
- Authors

- Name
- Alex Lee
- @alexjoelee
**FYI: **This post is part of a series where we're covering how to use and implement the Core Rule Set. Check our all of our special articles and tutorials for Cybersecurity Month 2023.
 Core Rule Set 3 poster by Hugo Costa, unmodified, original located here: https://coreruleset.org/poster/ Safeguarding web applications against nefarious activities is paramount. Among the myriad of tools designed to bolster web application security, the Open Worldwide Application Security Project (OWASP) Core Rule Set (CRS) stands out as a formidable shield against a broad spectrum of attacks. The CRS is a robust set of generic attack detection rules that provide a solid defense against various malicious attempts, making it an indispensable asset for cybersecurity endeavors.
Core Rule Set 3 poster by Hugo Costa, unmodified, original located here: https://coreruleset.org/poster/ Safeguarding web applications against nefarious activities is paramount. Among the myriad of tools designed to bolster web application security, the Open Worldwide Application Security Project (OWASP) Core Rule Set (CRS) stands out as a formidable shield against a broad spectrum of attacks. The CRS is a robust set of generic attack detection rules that provide a solid defense against various malicious attempts, making it an indispensable asset for cybersecurity endeavors.
Microsoft Internet Information Services (IIS) is a trusted, scalable, and flexible web server used by organizations worldwide to host their web applications. However, like any web server, IIS is susceptible to a variety of web application attacks. Integrating the OWASP CRS3 with Microsoft IIS significantly enhances its security posture, providing an automated defense mechanism against common threats.
Here's a closer look at why implementing the OWASP CRS3 with Microsoft IIS is a prudent move:
- Automated Detection and Prevention:
- CRS3 tirelessly monitors the traffic flowing through your web applications, identifying and thwarting malicious requests automatically. This continuous vigilance substantially reduces the risk of security breaches.
- Broad-Spectrum Protection:
- The comprehensive nature of CRS3 rules provides a wide-angle protection against numerous attack vectors including SQL Injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF), among others.
- Compliance and Reporting:
- Adhering to various regulatory and compliance standards is a requisite in today's business landscape. Implementing CRS3 facilitates compliance with industry standards, providing the necessary logs and reporting tools for audit purposes.
- Customizable Security Posture:
- The flexibility of CRS3 allows for customization to cater to the unique security needs of your organization. Fine-tuning the rules to align with your operational environment guarantees optimal protection without hindering legitimate traffic.
5.** Community-Driven Updates**:
- As a part of the reputable OWASP project, CRS3 benefits from continuous updates and improvements by a global community of cybersecurity experts. This ensures that the rule set evolves to counter emerging threats.
- Enhanced Performance:
- By filtering out malicious requests, CRS3 makes sure that your server resources are not squandered on processing harmful traffic, thus enhancing the overall performance and responsiveness of your web applications.
Implementing the OWASP CRS3 on Microsoft IIS requires using a compatible Web Application Firewall (WAF). Various WAF solutions are available that can be seamlessly integrated with IIS, facilitating the deployment of CRS3 and thus, fortifying the security perimeter of your web applications.
Install Microsoft IIS on Windows Server 2022
- From Server Manager, add a new Role or Feature
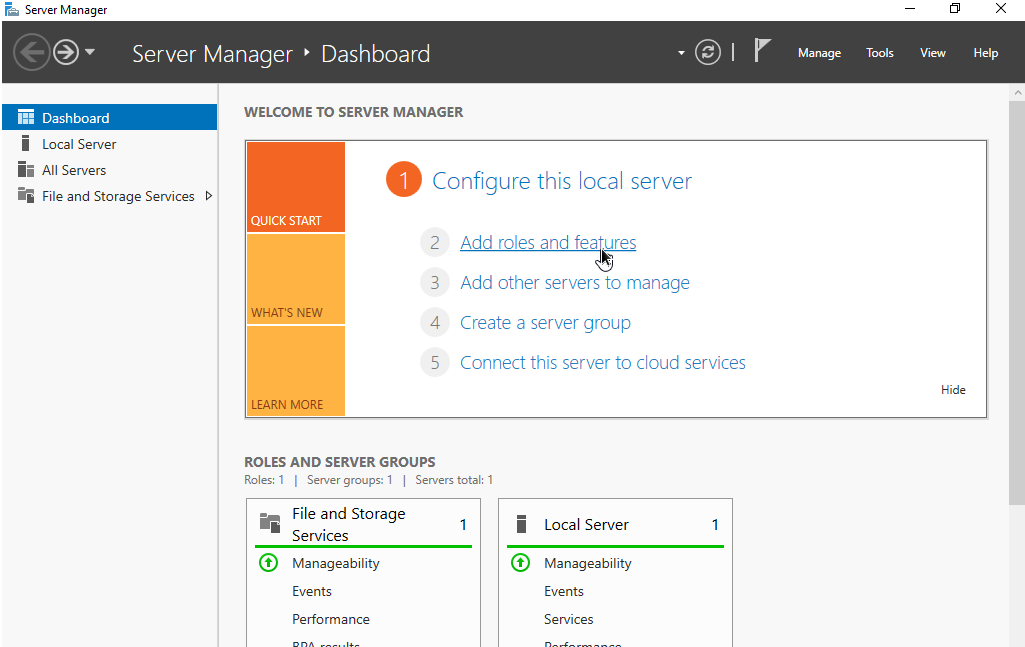 2. Follow the steps to install Web Server IIS - the defaults will do just fine here
2. Follow the steps to install Web Server IIS - the defaults will do just fine here 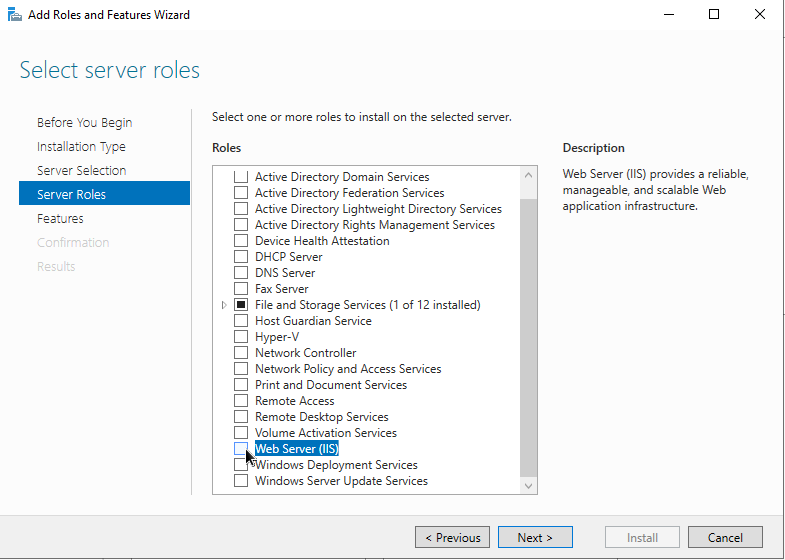
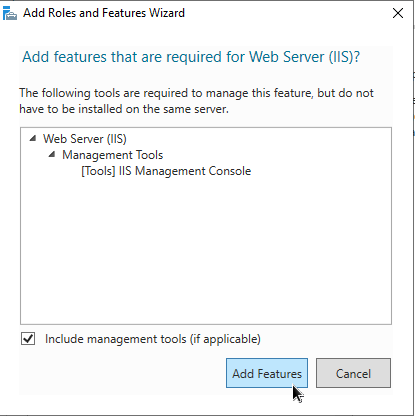
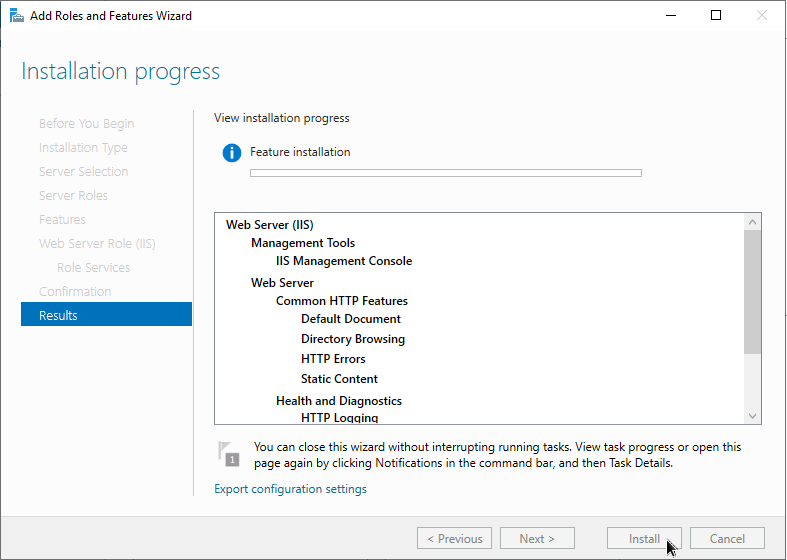
Install ModSecurity on Windows Server 2022
- Navigate to the ModSecurity Github Repository and find the latest .MSI release
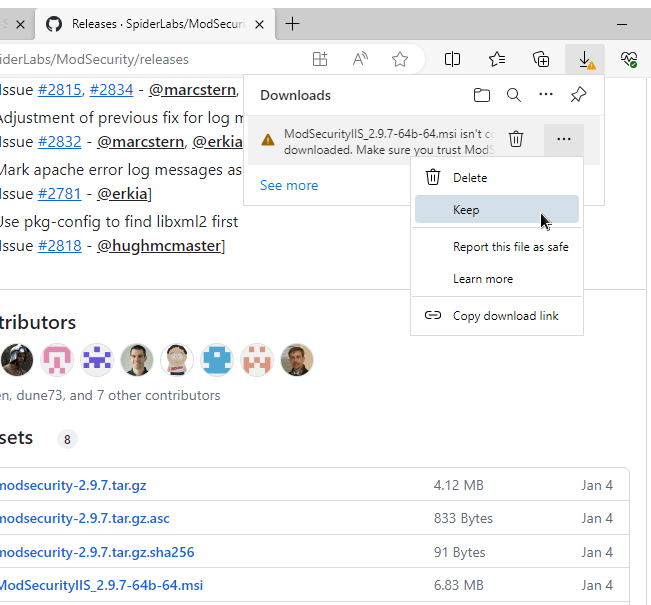
- Install using the default steps. You'll likely need to restart the server after the installation completes.
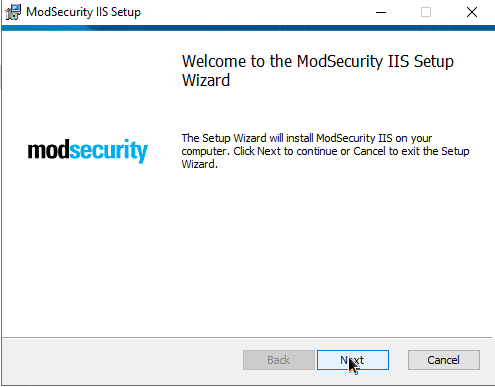
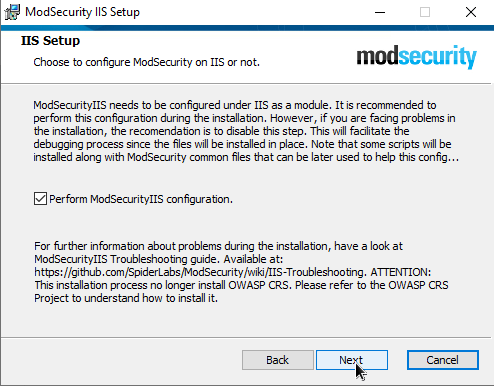
Download and Implement the OWASP CRS on Windows Server 2022
- Navigate to and clone the Core Ruleset Github repo
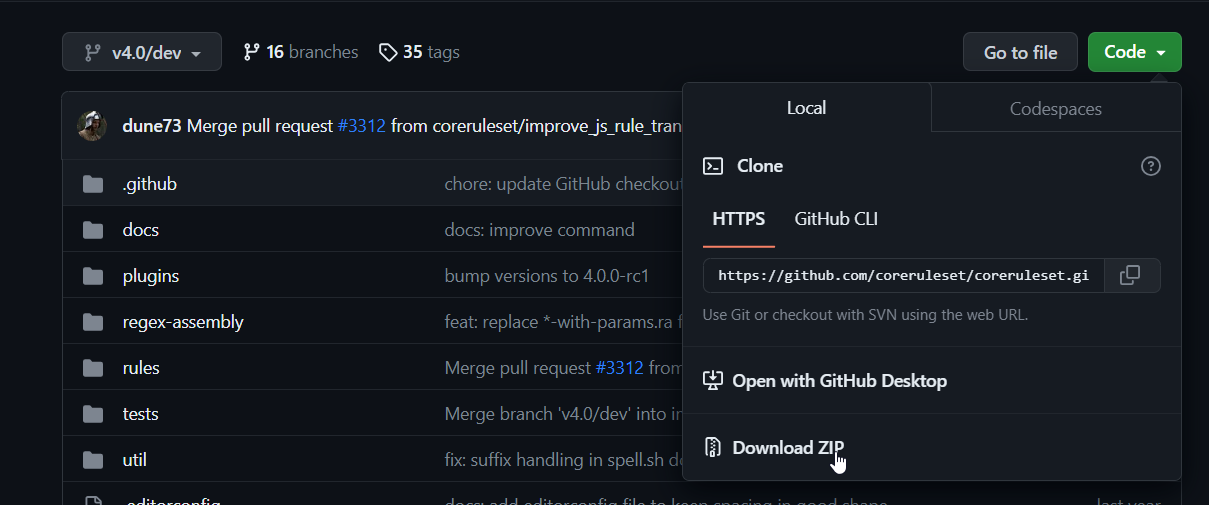 2. Install the rules folder and crs-setup.conf.example to C:\Program Files\ModSecurity IIS
2. Install the rules folder and crs-setup.conf.example to C:\Program Files\ModSecurity IIS  3. Remove .example from the rules and configuration files:
3. Remove .example from the rules and configuration files:
/crs-setup.conf*.example*
/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf*.example*
/rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf*.example*
To add the entire Core Rule Set to the configuration, your modsecurity_iis.conf should look something like this:
Include modsecurity.conf Include modsecurity_crs_10_setup.conf Include owasp_crs\base_rules*.conf #OWASP-Rules include owasp-modsecurity-crs/crs-setup.conf include owasp-modsecurity-crs/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf include owasp-modsecurity-crs/rules/REQUEST-901-INITIALIZATION.conf include owasp-modsecurity-crs/rules/REQUEST-905-COMMON-EXCEPTIONS.conf include owasp-modsecurity-crs/rules/REQUEST-910-IP-REPUTATION.conf include owasp-modsecurity-crs/rules/REQUEST-911-METHOD-ENFORCEMENT.conf include owasp-modsecurity-crs/rules/REQUEST-912-DOS-PROTECTION.conf include owasp-modsecurity-crs/rules/REQUEST-913-SCANNER-DETECTION.conf include owasp-modsecurity-crs/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf include owasp-modsecurity-crs/rules/REQUEST-921-PROTOCOL-ATTACK.conf include owasp-modsecurity-crs/rules/REQUEST-930-APPLICATION-ATTACK-LFI.conf include owasp-modsecurity-crs/rules/REQUEST-931-APPLICATION-ATTACK-RFI.conf include owasp-modsecurity-crs/rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf include owasp-modsecurity-crs/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf include owasp-modsecurity-crs/rules/REQUEST-941-APPLICATION-ATTACK-XSS.conf include owasp-modsecurity-crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf include owasp-modsecurity-crs/rules/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf include owasp-modsecurity-crs/rules/REQUEST-949-BLOCKING-EVALUATION.conf include owasp-modsecurity-crs/rules/RESPONSE-950-DATA-LEAKAGES.conf include owasp-modsecurity-crs/rules/RESPONSE-951-DATA-LEAKAGES-SQL.conf include owasp-modsecurity-crs/rules/RESPONSE-952-DATA-LEAKAGES-JAVA.conf include owasp-modsecurity-crs/rules/RESPONSE-953-DATA-LEAKAGES-PHP.conf include owasp-modsecurity-crs/rules/RESPONSE-954-DATA-LEAKAGES-IIS.conf include owasp-modsecurity-crs/rules/RESPONSE-959-BLOCKING-EVALUATION.conf include owasp-modsecurity-crs/rules/RESPONSE-980-CORRELATION.conf include owasp-modsecurity-crs/rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf
Restart IIS and you are all set. Check the audit logs to ensure that ModSecurity is running properly.
You have now successfully implemented IIS, ModSecurity, and the Core Rule Set on your Windows Server 2022 machine. This is a significant stride towards fortifying your server against a myriad of web-based threats. By integrating ModSecurity and the Core Rule Set, you've not only enhanced your server's security posture but also laid a solid foundation for further security optimization in the future. Your proactive approach in following this tutorial underscores your commitment to creating a robust, secure environment for your digital assets. As you move forward, you'll find the knowledge acquired here to be an asset in managing and safeguarding your server infrastructure. The journey towards a secure server doesn't end here; it's a continuous endeavor, and this implementation has positioned you well on that path.