- Published on
All you need to know about E-mail Spoofing and how DNSSEC helps
- Authors

- Name
- Alex Lee
- @alexjoelee
What is e-mail spoofing?
Email spoofing is a digital impersonation tactic often used in phishing and spam campaigns. It occurs when an attacker sends an email that appears to come from a trusted source, but in reality, it's from a completely different sender. The objective is to trick the recipient into opening the email and possibly clicking on a malicious link or sharing sensitive information.
To understand how email spoofing works, one must first grasp the basics of the Simple Mail Transfer Protocol (SMTP), the standard for sending email across the Internet. When an email is sent, SMTP doesn't provide any authentication. This lack of verification allows an attacker to masquerade as someone else. They can manipulate the "From" address and other parts of the email header to make it appear as if the email was sent from a trusted source, such as a bank, a colleague, or a reputable company. The malicious email might ask the recipient to share sensitive information like passwords or credit card details, or it might contain a link to a malicious website.
The consequences of email spoofing are far-reaching and can significantly impact both businesses and individuals. For businesses, an effective spoofing attack can lead to unauthorized access to sensitive company data, financial losses due to fraudulent transactions, damage to brand reputation, and a decrease in customer trust. Individuals who fall victim to email spoofing may experience identity theft, financial loss, and a breach of personal data.
Given these potential impacts, understanding and preventing email spoofing should be a priority for everyone in the digital space, particularly service providers, as these networks can be exploited to disseminate spoofed emails more widely and quickly. 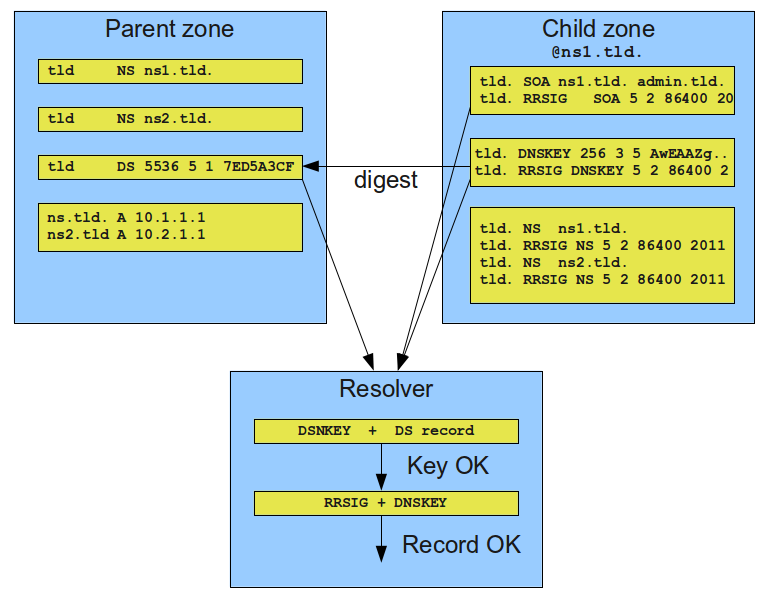 "File:DNSSEC resource record check.png" by Kaaa is marked with CC0 1.0. An Introduction to DNSSEC
"File:DNSSEC resource record check.png" by Kaaa is marked with CC0 1.0. An Introduction to DNSSEC
The Domain Name System Security Extensions (DNSSEC) is a suite of Internet Engineering Task Force (IETF) specifications designed to secure certain kinds of information provided by the Domain Name System (DNS) against forgery and attacks. The DNS is responsible for translating human-friendly domain names into numerical IP addresses that computers use to communicate. However, it was not originally designed with robust security measures, and as a result, it is susceptible to attacks such as DNS spoofing or cache poisoning.
DNSSEC adds an essential layer of security to the DNS by authenticating the origin of DNS data and ensuring its integrity during transmission. It accomplishes this through a system of public keys and digital signatures. Here's how it works:
- When a DNS resolver, like your internet browser, makes a request for a site, it also requests a digital signature.
- The server responds with the DNS response and a signed digital signature.
- The DNS resolver then uses a public key to authenticate that the signature came from the stated sender and that it hasn't been tampered with.
If the signature doesn't validate, the resolver can make the assumption that there's a security risk and refuse to complete the request. The entire process is seamless to the user and happens in milliseconds.
DNSSEC plays a critical role in preventing email spoofing. As we've seen, email spoofing often relies on the manipulation of DNS data. By ensuring the authenticity and integrity of this data, DNSSEC makes it significantly more difficult for attackers to redirect or intercept emails. It can prevent attackers from masquerading as legitimate entities, thereby reducing the risk of successful phishing attacks.
For those using custom e-mail, the importance of DNSSEC cannot be overstated. It adds a layer of trust and security to the network, ensuring that users are communicating with the intended parties and protecting against the distribution of spoofed content.  "Phishing warning" by Christiaan Colen is licensed under CC BY-SA 2.0. The Connection between Email Spoofing and DNSSEC
"Phishing warning" by Christiaan Colen is licensed under CC BY-SA 2.0. The Connection between Email Spoofing and DNSSEC
Understanding the relationship between email spoofing and DNSSEC is fundamental to comprehending the broader picture of internet security. As we've discussed, email spoofing is a common cyberattack where an intruder sends an email that appears to be from a trusted source. This tactic often manipulates the DNS system, exploiting its inherent trust and lack of verification. DNSSEC, on the other hand, adds a layer of security to the DNS system, helping to guard against such manipulations.
DNSSEC protects against email spoofing by ensuring the authenticity and integrity of DNS data. When an email is sent, it relies on DNS to direct it to the right server. If a cybercriminal attempts to spoof an email, they may try to manipulate DNS data to misdirect the email or impersonate a trusted entity. DNSSEC combats this by providing a method to check whether the DNS data is genuine and unchanged, thereby making it significantly harder for an attacker to successfully spoof an email.
While it's challenging to provide specific real-world examples of DNSSEC preventing email spoofing (mainly due to the confidential nature of cybersecurity incidents), there are well-documented instances of DNSSEC mitigating similar attacks. For instance, the DNS-based phishing attack on the Brazilian bank, Banco de Brasil, in 2018 could have been prevented if DNSSEC was implemented. The attackers hijacked the bank's domains and redirected its customers to perfectly cloned sites, leading to massive phishing and the potential for spoofed emails. DNSSEC, with its capacity to validate the authenticity of DNS responses, could have alerted both the bank and its customers to the attack, thereby preventing the domain hijacking that facilitated the attack.
Conclusion
Email spoofing, a common yet dangerous cyberattack, involves the forgery of email headers so that the message appears to come from someone other than the actual source. It's a tactic used to deceive recipients into revealing sensitive data, enabling unauthorized access, or unknowingly spreading malware.
DNSSEC serves as a powerful shield against such threats. It's a suite of extensions that add a layer of security to the Domain Name System, which can otherwise be exploited by attackers. By validating the authenticity and integrity of DNS data, DNSSEC thwarts attempts to misdirect or intercept emails, making it a potent defense against email spoofing.
As the next steps, consider the practical implementation of DNSSEC, learning from real-world examples and potential threats. Prioritize educating your teams and users about the risks of email spoofing and the protective measures available. The journey towards a safer and more secure internet continues, and every step taken in knowledge and defense counts.